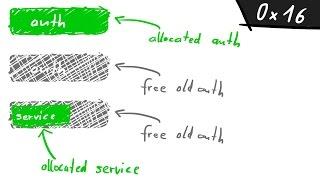
Exploit Operate
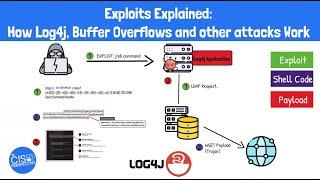
Exploits Explained: How Log4j, Buffer Overflows and Other Exploits Work
The CISO Perspective
5K
15,925
2 года назад
Unbox Aruba AP11 Instant On and Configure in Manage WEB Portal 2024
Exploit & Operate
137
458
7 месяцев назад
Demonstrating how Hackers search for exploits and Launching an attack with metasploit
StealthyCyberTaco
4K
14,399
2 года назад
Сейчас ищут
Exploit Operate
Anime Fighting Simulator Hacks
Killer Instinct Обзор
Семинарайкидо
Msfs Name On Aircraft
Happy New Year Script Code For Blogger
Анонсы И Карусель Весна 2016
Nick Jr Deutschland
Upin Minecraft
Restaurants Closing
Хуторянка Блогер
Комбайнеры
Blocksy Theme Sticky Header
Mek Sarrah Hijab Style
Кобра Клип
Приколы Про Марки Машин
От Морщин Под Глазами
Вики Шоу Видео Про Новый Год
Video Timeline Photoshop
G И M Коды
How To Rank Website On Google First Page
Phone Shipments
Anime Industry
День Ангела Ольги
Host Explorer
Реш Еду Баги
Sadie Pantyhose
Shrek The Third Hd
Kunjan Hub
Saneub
Song Ca Phi Nhung Mạnh Quỳnh
Липовый Мед Чем Полезен
Exploit Operate смотреть видео. Рекомендуем посмотреть видео How Do Exploits Work? длительностью 5:46. Invideo.cc - смотри самые лучшие видео бесплатно