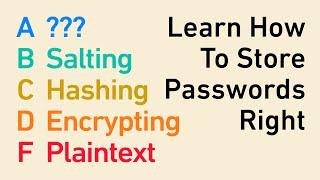
Password Storage Tier List: encryption, hashing, salting, bcrypt, and beyond
Комментарии:
Password Storage Tier List: encryption, hashing, salting, bcrypt, and beyond
Studying With Alex
Free Flp Project | Cg Remix | Cg Dj Song | Dj Durgesh
DJ DURGESH KSL
aiste pilvelyte - leisk sau
zasinelis
Фильм про заключенных в тюрьме будущего. Крепость!
Кинофильмы и сериалы смотреть онлайн
ТЫ - ДУША МОЯ. РАДА РАЙ. ПОЁТ ЕЛЕНА БОРТНИКОВА.
Елена Бортникова -Душа поёт.
HELLUVA BOSS - MASTERMIND // S2: Episode 11 REACTION!!!
Steven Z KILLER