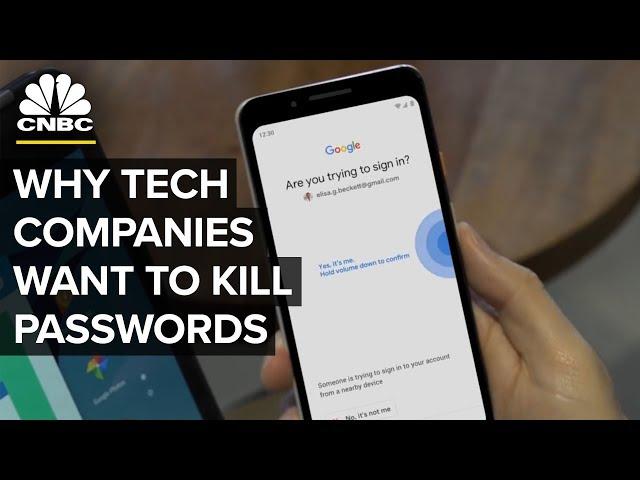
Комментарии:

The answer is Biometrics very simple because nobody has the same Biometrics in the planet problem solved and firewalls that recognize just Biometrics for the account holder.
I can't believe there are still idiots who ask you to change your password (hackable) every 60 days and thats the most IGNORANT!!! policy companies do.
Statistik from every 2,000 people just one or two people know really well
the Technology and tge rest are just users,customers and you are going to need to be a Rocket Scientist to use a phone or computer ? jajaja no phones will be ever sold if that is the case

How bought instead of DHCP and flexible Ip addresses we move toward fixed ones that are not assigned every connection, but every 90 days, then make the password only recognizable from THAT IP address. It seems the flexible arrangement of the DHCP scheme is the weak link in the chain.
Ответить
Ah yes, i will allows my device which the company can spy on and lock because youre mexican to have my fingerprint/face identity to have it sold on the dark net
Ответить
What if your dead
Ответить
You will never get me to go passwordless. It's too dangerous. If my phone is lost, stolen or destroyed, I lose ALL my login ability...
Ответить
I have only few passwords that I remember ( and that I use every day ) - those to unlock phone and computer and the one to unlock encrypted KeePass database. After which I can just copypaste my passwords for website, which are 24 random symbols. KeePass and password managers in general are really useful software
Login via biometrics is kinda controversial and has it's limitations. It raises three questions:
1) If we are talking about encrypted devices and databases, how the encryption keys are going to be derived from your face id or fingerprint?
2) How easy is it to falsify biometrics - back in the days I have bypassed FaceID using a photo, not going to work with strong password
3) How bad is biometric authentication for your privacy?

One problem with Yubico keys is if its lost, you are seriously screwed. A friend of mine lost her yubico key and could not ever log back on to Windows.
Where she has her work documents that had to be handed in that following Thursday. Since she was locked out of her computer and no way to recover from the lost key.
She was fired for missing the deadline of her meeting that she had to hand in and also present during a very important meeting in a venture fund company.
In order to be some what secured from that major problem, you have to invest in more than 1 key and at the minimum have 4 keys as backup to your primary.
To make sure you don't lose your authorization to log into devices that may have extremely important job related items.
Or even personal items as well.
Also these companies say that the FIDO is saved within the device and thats how people log in and they say its secure. Well its really not.
What if you lose your device, or or get robbed or mugged from your device. What then? If the authorization is on the device, how can you log into your accounts,
if someone stolen your device or your device got lost. See, there are major loopholes that no one realizes. And this is a major problem.
TPM's don't work either because if you lost the device, you're pretty much screwed.
And as far as companies (claiming) that they don't store your biometrics, is a complete lie. They do save your biometric, just like Amazon saves your voice
and anything you say permanently on their server forever and you can't delete it. Don't ever believe a major company when they say they don't store anything.
Facebook said the same thing, and look at what they did with peoples data. They even ended up in court. And even the EU had to change and implement laws for the GDPR.
Using biometrics will automatically hand over your identity to major corporations and they will know who your are, what you are doing and your current location.
Where are you logged in and for how long. And to put matters worse, they keylog everything you do.
Don't believe me, here is one proof out of millions. When you install Windows 10 or 11, the very first thing you have to agree to, is microsoft to log your keystrokes.
And there is a switch that says you can turn it off, but it really isn't turned off. Its false sense of security making you think its off, but its still on.
Many security experts revealed this little nugget and did a report about it.
Microsoft even admitted it, right within their operating system, by telling you that they will log keystrokes. 💀💀💀
Yes people swear by FIDO keys, but they don't tell you the dangers of it. They don't tell you the downsides and what happens if you lose it.
FIDO has yet to solve that major problem. If you lose your key that has login passwords for all your work and personal accounts. Your entire life is locked away if you lose your key or keys.
Maybe we need a permanent body chip as a FIDO key. so we can never lose it. But then that in itself will open a whole new can of worms. 🤷♀🤷♀🤷♀
Welcome to the human race. 🤦♂🤦♂🤦♂

Funny how the new MS CEO talks just like Bill Gates, I couldn’t hear any diff
Ответить
its a matter of control
Ответить
From what I understand 'FACE' recognition technology is NOT built to recognize BLACK FACES! What are you doing about that?!!!! Also, my fingerprints are VERY LIGHT and hard for computers to read. I know this for a FACT!
Ответить
Just to let people know the modern high end computers can break a 8 digit password in 48 mins
Ответить
My former password for all devices and accounts: @gentSmith_1984. Agent Smith is my favorite movie character of all times and 1984 is a great novel by George Orwell. My current password is more harder to decode but more easy to remember.
Ответить
My parents don't even bother using their pin code or fingerprint or face I'd.
Ответить
We must nationalize all the company and banks,regulate commodities purchase and create education with production at national cost
Ответить
Kevin is a fake hacker... He made deal with the government to help them, most hackers not allow to use computer after getting busted. just like criminal they cant own guns , kevin caught using a computer to commit crimes.
Ответить
Here is an example of a 128 character randomly generated password. It would take 23 billion septuagintillion years to crack.
1B1^5H@N96$40VHMY5KZbx7zkM6G%BsHc2G08nd2fJ9EHoL1w4PER0WR964M2kx@R4^scfzrAkb@6*$kig$Ld*upI2tL$OPD79qTMqWL8CCNB8Utg!HtjG6Doh9XXnDX

21. isi An Rom e egg V egg head
Ответить
N3 🦆1 Mobile know who we are looking
Le Öe 11 E 2 id Robe

Android We Partners Mobile will remember
The pass 1 Secrate nr.or 🦆 icon will work for all
Password. Numbers are Crazy to remember.
TMC 🐅 Media 🦆 TaiduTiger

I use a bookmarklet to compound a site url in the hash section ciphered user pass pair under a PIN number. If there is no hash section, it collect fields user and pass value, ask for a pin generating a LOGINURL in address bar that you can bookmark or copy. If bookmark contain a hash section you are prompted for a PIN, user pass are decyphered, to fill respective fields and SUBMIT triggered. Most of browsers know how to sync bookmarks between themselves, so you don't need to store bookmarks on Cloud or USB key. The process run within login page, nothing is typed on the keyboard, process stay in vacuum.
Ответить
Finally thumb print coming back
Ответить
the dude at 1 minute sounds like patrick bateman
Ответить
So if face ID is 1 in 1,000,000 then that means that in a world population of 7,753,000,000 there are 7,753 people on the planet that can break your biometric. I know that sounds small, but do you know what is even smaller... a 16 character password. Additionally... a fingerprint and a face DO NOT require a warrant or subpoena to acquire. If you are arrested and the police wanted to get into your face ID phone all they have to do is show it to you and it will unlock. That being said... a 4-digit pin (super easy to force crack) still requires a subpoena to acquire. Face ID or a fingerprint do not subvert your 5th amendment, "shall be compelled in any criminal case to be a witness against" themselves. If A cop simply picks up your phone turns it to face you and it unlocks... that doesn't present a breach in your 5th amendment right. Therefore, a pin or a password are actually more secure than a fingerprint or a face ID.
Ответить
yeah well, I cant get into my email now that i changed my number. Thanks Google.
Ответить
so when somebody breaks into your house they can just grab you in front of your computer and log into your bank and clear your accounts at the gunpoint which would be prevented by a password
Ответить
Convenience is the path to control... ask anybody in China.
Ответить
Yeah, let's just grab all perfectly working devices that lack biometric detection and throw it in the garbage, such a good idea.
Ответить
Maybe they’ll have brain scan technology as well someday in the future and I can show the staff at school waiting for my brain scan on the gagging thing
Ответить
how is the image of my face supposed to be something no one has, when it’s right out in plain sight?
Ответить
Check this out, I use fingerprint to unlock my phone but after re-wiring my basement lights, my fingerprints were altered by small cuts. This meant I was no longer able to use fingerprint unlock on my phone until they healed. Imagine if I did not have another way to unlock my phone and needed to call for help.
What if you used face recognition and you had an accident and your face was damaged and could not get emergency assistance.
I do use passwords but I also use two step verification including text pin and fingerprint. I also store my passwords on a secure NAS behind a firewall and a DMZ with fingerprint login.
I keep my phone unlocked for up to 4 hours as long as I am at home and when I leave home, it automatically locks both my phone and my home. My smart home does some amazing things when it sees my phone get home, but I still need to enter a 16 digit code to let it know I am also accompanying my phone. Then I use a second step voice verification using good & bad word in case I am under duress. There are 2 - 16 digit codes as well, one for normal and a second when I am under duress. I do not always need to authenticate by voice, but I have it in case and it its trigger is secret and separate from the good code. The reason I bring this up is to say there are more than these 3 ways mentioned in this video to authenticate, what you know, what you have & who you are. A clue is from IFTTT (if this then that). This can include activating or deactivating separate smart devices, and timing between each. All hidden within routines and or subroutines. Both virtual and real devices. I know that this is just a combination of all 3 but the next part is by changing & encrypting the variations of how they are used and the timing between them. This is like the RNG to know which of the two step verification to use based on an IFTTT.
Fast forward to the future where passwords have been eliminated. Now all logins are bio-metrics and your face is replicated by AI on a hologram. Your phone has been cloned and your fingerprints are for sale on the dark web as gloves you just slip on like a thief does before entering your home. Your iris is sold on the dark web as a pair of contact lenses.
Bio-metrics only use some of the five senses we have, touch, sight and hearing. There can be smell and even taste added to ensure you smell or taste like you. Then if we go deeper we can even use DNA. How about unlocking AI to include reading what we are thinking or feeling.
Locks on doors are not there to keep criminals out, they are there to keep honest people honest. To be safe, all we need to do is have harsher penalties for bad actors. As it is now, if a criminal breaks into your home, they can sue you if they get hurt in the process.
I see the next evolution is to have chips implanted. This is the last step before the end, the real end. Y'all know what I'm talking about.

lets welcome to brainless/useless human era, incapable to remember where their brain is......wake up!...remember the movie, IROBOT?.. ft Will Smith?...my opinion....
Ответить
MARK of the beast
Ответить
More of my fellow millennial coworkers use a password manager than not. This is (once again) the boomers’ fault.
Ответить
I just use my fingerprint on my phone cause it is more conventional
Ответить
The digital realms are destiny?
Ответить
Hackable OS is created by humans, all source code is easily understood by a human. An OS must be created by AI that the future has no more hackers.
Ответить
Except people are covering their webcams. 😆
Ответить
Aa mansante satyasanthatha😂😂😂
Ответить
My work's email has a 32 character password with all these requirements like no more than 2 consecutive classes of characters in a row and insane rules like changing every 30 days or 7 days if not used and can't be similar to any passed passwords. So what we do is have computer generated passwords we use that are written down.
Ответить
What about a password manager? 🤦♂️ People don’t use them! They’d rather use Kentuckywhiskey as there password! 😆
Ответить
Hmmm im reluctant to this... if you register your e.g., finger print or face in some website... does that mean that website can unlock any of your account somewhere?
I think we should move to 2FA (2-factor auth) is good,
1. Password authentication
2. biometric/phone.
I dont like the idea that you can login using biometrics only. Shouls be 2-fa

This was spot on
Ответить
That website was seized lol
Ответить
Thank you, FINALLY someone realizes how easy it would be to spoof a 2FA request. Too bad he was biased or wrong about basically everything else. 🙃
Ответить
Ok then, for my online bank account, I should just rely on the honor system?
Ответить