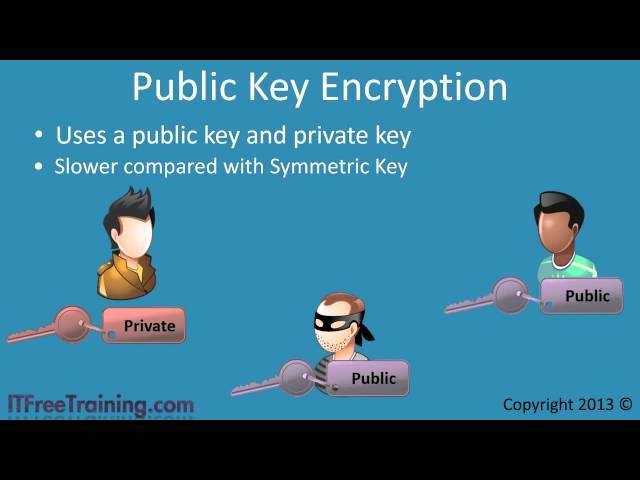
Symmetric Key and Public Key Encryption
Комментарии:
GOT7 - 니가 하면 (If You Do) (Audio)
Rubik Music
How to make custom prefix of your discord bot (NO CODING)
BRANDON GAMERZ
DELL XPS 8930 Disassembly RAM SSD Hard Drive GPU Upgrade PSU Power Supply Replacement Repair
It's Binh (Been) Repaired & Everything Reviewed
Symmetric Key and Public Key Encryption
ITFreeTraining
This Used to be the KING of Budget Gaming PC's! #optiplex #pcbuild
YourPersonalGeek
ЧТО МОЖНО НАЙТИ ПОИСКОВЫМ МАГНИТОМ
ФАРТОВЫЙ ПОИСК НН