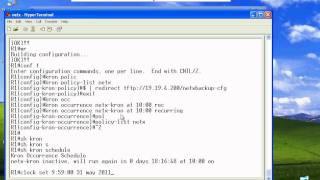
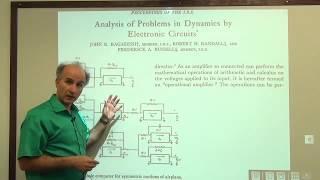
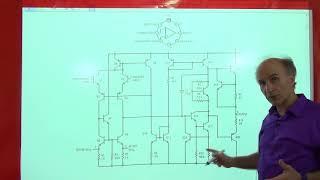
Hack The Box Lame Walkthrough (full) // OSCP Prep
A deep dive walkthrough of the responder machine on Hack The Box. Learn how to pentest & build a career in cyber security by starting out with beginner level walkthroughs like this!
------- Contents of video -------
0:00 - Intro
1:30 - Enumeration
5:00 - Anonymous FTP
6:25 - SMB Enumeration
11:45 - Identifying known Exploits
14:00 - Initial Foothold
Zero Point Security Courses (Affiliate Links):
Red Team Ops - https://courses.zeropointsecurity.co.uk/courses/red-team-ops?ref=671bbb
C2 Development in C# - https://courses.zeropointsecurity.co.uk/courses/c2-development-in-csharp?ref=671bbb
Offensive Driver Development - https://courses.zeropointsecurity.co.uk/courses/offensive-driver-development?ref=671bbb
My GitHub Repo (with notes on topics used in this video): https://github.com/jakescheetz/OSCP
In this video we work through the machine "Lame" on @HackTheBox . We look use and analyze known vulnerabilities on the target and then gain an initial foothold on the system from that enumeration. This machine is apart of the community curated list of Hack The Box machines that prepare you for the OSCP exam.
#hackTheBox #walkthrough #lame #tutorial #capturetheflag #oscpPrep
------- Contents of video -------
0:00 - Intro
1:30 - Enumeration
5:00 - Anonymous FTP
6:25 - SMB Enumeration
11:45 - Identifying known Exploits
14:00 - Initial Foothold
Zero Point Security Courses (Affiliate Links):
Red Team Ops - https://courses.zeropointsecurity.co.uk/courses/red-team-ops?ref=671bbb
C2 Development in C# - https://courses.zeropointsecurity.co.uk/courses/c2-development-in-csharp?ref=671bbb
Offensive Driver Development - https://courses.zeropointsecurity.co.uk/courses/offensive-driver-development?ref=671bbb
My GitHub Repo (with notes on topics used in this video): https://github.com/jakescheetz/OSCP
In this video we work through the machine "Lame" on @HackTheBox . We look use and analyze known vulnerabilities on the target and then gain an initial foothold on the system from that enumeration. This machine is apart of the community curated list of Hack The Box machines that prepare you for the OSCP exam.
#hackTheBox #walkthrough #lame #tutorial #capturetheflag #oscpPrep
Тэги:
#HackTheBox #htb #starting_point #starting_track #pentesting #security #walkthrough #cyber #tutorial #cybersecurity #hacking #ethical_hacking #ethical_hacker #learning_to_hack #responder #hack_the_box_lame #lame_hack_the_box #lame_hack_the_box_walkthrough #lame_htb_tutorial #htb_lame #lame_htb_walkthrough #lame_htb_starting_point_tutorial #starting_point_htb_lame #walkthrough_htb_lame #oscp_prep #oscp_prep_hack_the_boxКомментарии:
Hack The Box Lame Walkthrough (full) // OSCP Prep
FindingUrPasswd
Razavi Electronics 1, Lec 42, Op Amp Circuits 1
Behzad Razavi (Long Kong)
How to upgrade your Tools in #occupymarsgame #gaming
Nasomies Gaming
Razavi Electronics2 Lec1: Introduction, Cascode Current Sources
Behzad Razavi (Long Kong)
Occupy Mars: The Game - Early Access Trailer
ThePlayWay
How to Configure the Backup and Restore on Cisco DNA Center
Cisco Catalyst Center
Razavi Electronics 1, Lec 29, Intro. to MOSFETs
Behzad Razavi (Long Kong)