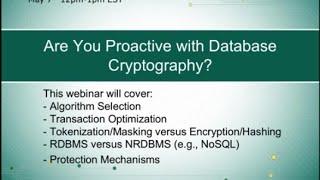
Proactive Risk Presents: Database Cryptography w/ Steve Markey
This webinar will cover:
-Algorithm Selection
-Transaction Optimization
-Tokenization/Masking versus Encryption/Hashing
-RDBMS versus NRDBMS (e.g., NoSQL) Protection Mechanisms
For more information about information security services visit Proactive Risk at www.proactiverisk.com
-Algorithm Selection
-Transaction Optimization
-Tokenization/Masking versus Encryption/Hashing
-RDBMS versus NRDBMS (e.g., NoSQL) Protection Mechanisms
For more information about information security services visit Proactive Risk at www.proactiverisk.com
Тэги:
#Database_(Software_Genre) #Cryptography_(Software_Genre) #Web_Application_Development_(Industry) #OWASP_(Business_Operation) #algorithm #rdbs #nosql #database #development #security #testing #hacking #hacker #nyc #proactive_riskКомментарии:
Фестиваль Троица. Все Живое 19.06.2016 канал ютуб: Игорь Осипов Квартирники Москвы
Игорь Осипов (Квартирники Москвы)








![АНОМАЛИИ В СТРАШНОМ МЕСТЕ! - Project 13: Taxidermy Trails [Хоррор Стрим, Прохождение] АНОМАЛИИ В СТРАШНОМ МЕСТЕ! - Project 13: Taxidermy Trails [Хоррор Стрим, Прохождение]](https://invideo.cc/img/upload/QW14dXpLWnBkaUI.jpg)