Комментарии:

After giving the command " shred - vfzu auth.log". It shows "Shred : auth log failed to open for writing: operation not permitted "
Kindly give the solution

the program shred the files, should have a amnesic part that forget how it had over write the file. kind of using rust or nim and no c or c++ that use other part of memory to do a new task.
Ответить
but why not just put all to 1 or 0 . all. the file size.
Ответить
I used covermyass from github...it did way more task than mentioned in video ....but server admin still know what I'm been doing ...maybe from last modification date
Ответить
Cheers Mate.
Ответить
Since there is no Windows video yet, does anyone knows an alternative for windows machines?
Ответить
Hey Mr HackerSploit, thanks 👍
Much love from share

Очень много говорит и очень мало делает
Ответить
ALL INTEGRATED CIRCUTS SHOW TRACKS AND IS DOWNLOADABLE FOR USE IN ANY DIRECTION AND THEN IT'S ANALYZED FOR BEHAVIOR COOL RIGHT
Ответить
The best explanation and illustrations ever you are the world's best teacher
Ответить
The world's best teacher thanks
Ответить
Can you make a video on how submit report after pent testing?
Ответить
If your on live os , this aint needed , anyway good informative vid !💯
Ответить
Hackersploit is best english hacking channel 😎
Ответить
Very useful and awesome video
Ответить
How to clear ufw.log file, kern.log and syslog.
Ответить
Shredding important log files is not preventing the system to work as intended ?! Lets suppose i am pentesting a Linux Machine ,Is it not easier to backup all the log files at the exact moment when i log into the machine ,And after my changes in the FIlesystem ,I simply replaced the modified log files with the original one ? ( Ofc deleting the later generated entrys from the log files like auth.log and .bash_history , etc )
Ответить
great video ,thanks
Ответить
5 minute only speak hmm
Ответить
you are the best Linux teacher
Ответить
What if we shred the entire log directory
Ответить
okay i agree about clearing logs and backdoors! but how if the forensics team recover all the deleted data over the device! its just an old trick now the nsa have a big technology helping them to finding the hackers like over communication gsm-line but if you hack the server and exploit the root privileges to editing the virtual ip it will be fine!
Ответить
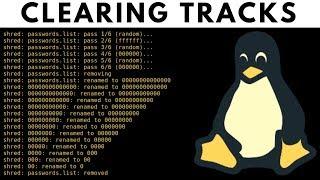
why is the file renamed to 000000 then 00000 then 0000 then...
Ответить
macos getting popular among pentesters?
could someone explain this

Does overwriting the file with null can't be recovered????
Ответить
For Windows also..
Ответить
what about journal logs? pretty important
Ответить
I wonder what if the company actually pipes logs to another server, then stores them in a very unusual place with an unusual name
Ответить
so i have to shred all the file that have a .log in my linux to make it clean?
Ответить
I appreciate the video sir alexis! :) how about tracks on the remote computer?
Ответить
This is actually important.
Ответить
the best thing i should have learned for hacking practice. thank you so much for this tutorial you are doing a great work.
Ответить
Just wow
Ответить
Command history is appended to the file whose path is stored in the variable "$HISTFILE", but only AFTER you have ended your session. HISTFILE is automatically set to ~/.bash_history for each new shell.
TL;DR
Just type HISTFILE=/dev/null when you're hacking and nothing will be saved in .bash_history

شرح اكثر من رائع :)
Ответить
Please do make the windows and macOS version next, it would be nice while the knowledge is fresh :-)
Ответить
How can I replace windows 10 with kali linux 2018.4 permanently help me plzz upload video
Ответить
1.hey Hackersploit can you tell me something about this LAN tap all ATM machines are working on LAN is this possible to sniff ATM transaction
2. is that possible Hackers can intercept ATM machine that i am using for my transaction ???

Just a little tip for you : You can clear the console by pressing "CTRL+L", it's way faster than typing "clear<ENTER>"
Ответить
How can I done it in Android termux
Ответить
thank you
Ответить
Nice tutorial! Is it also valid for SSD?
Ответить
Thank you very much for making this video... i learned lot of things from this...
i hope & i wish that u will make sime informative on Cyber forensics in detail ...
Waiting for it...

PAX invictus , namaste !
Ответить
I love your videos dude keep doing this you're awesome!
Ответить
We learned a lot, thanks
Ответить






![iOS 17 Jailbreak [Cydia+Sileo] How to iOS 17.3.1 Jailbreak iPhone/iPad iOS 17.4 Jailbreak! iOS 17 Jailbreak [Cydia+Sileo] How to iOS 17.3.1 Jailbreak iPhone/iPad iOS 17.4 Jailbreak!](https://invideo.cc/img/upload/SVlCTDhHUE5VeUk.jpg)

















