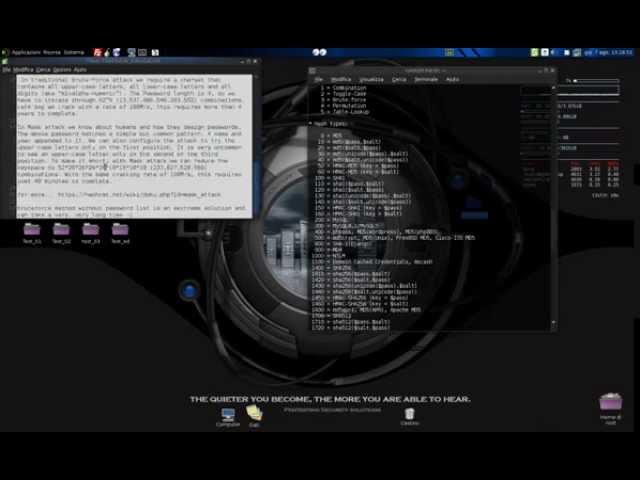
Crack Hash with Hashcat (Kali Linux) bruteforce (NO Password List) Tutorial
Комментарии:

Now we could use hashcat alphanumeric with cloud gpu minining . I think it would take less than years to complete .
Ответить
That song reminds me of Tom n Jerry
Ответить
Outdated doesn't work anymore!
Ответить
You cant even see what you are doing
Ответить
What version hashcat it is
Ответить
thanks 4 kali and cats)
Ответить
another bullshit that starts from the middle. you definitely have no mouth but a second ass hole, good for you, you become more and more popular. BRAVO
Ответить
hi how to decrypted sha256?
Ответить
how can i know the type of hash when i hack sites by sql injection because i have big problem about sql hash like these hash
$2y$10$LTWKkeKn.GZTifLOJSLVeuUb.jJFFQuEE6/swj6RM.3U4EZps8/sS
cc9425bbaa827b9dc6643e9bcf4454be
8143dd1b0014eeba1ac2ee77103586c
Kdvj4y7RAOol6GYs7/HCuJgZ8th8Q8Ra6YhrNA==
VIEPVm5B3W57mgYWVFMDE8aFnDezYQfwaGWrQD/2
UPh+dhEHdIc9gZ8kU1DeIXOt6pLobkIGre28O95H
zYqleq3jGcss/F8Xo2keDmo0B5+aI/eO7b0wEw==

?
Ответить
very beautiful music, thank you for the video, grazie mólto.
Ответить
Would a a GTX 670 be a viable card to use hashcat with to crack a wpa2 ?? with looking to do A-Z or and 8 characters long password
Ответить
How much time did it took up to give the exact password.....?????
i hv been sitting for about an hour nd half.....
but still its executing.........................................................
i hv a CPU device nd nt a GPU one ....thats what the prob. is...

If you don't know the victim password or have a skill slightest clue, how on earth will hashcat help me come close within the proximity range ?
Ответить
Hey man! Good night! How i use crunch to generate a live wordlist for oclhascat? (Like when somebody use, for example: # cruch 8 8 1234567890abcd | aircrack ... But with oclhashcat) Highest wordlist is very big for my memory! Sorry for my ultra wrecked english! I'm brazillian! lol
Ответить
spanis plis
Ответить
what Os?
Ответить
what theme are you using?
Ответить
WPA/WPA2 key version in your .hccap file is invalid
Ответить
Just liked for the music, bro ;D
Ответить
hello sir
when i tryed to decrypt hash using same comand dat u did i got that message
--pw-max is a reserved parameter for PRINCE attack mode can u help me plz

d6f515655cb604924d7370284bf6937c crack this if pro!
Ответить
Is that an overlay you are using on the far right of your screen? If so, may I ask which one?
Ответить
root@root:~# hashcat -m 0 -a 3 -n 32 --custom-charset1=?l?d?u --pw-min=6 --pw-max=8 /root/Desktop/hash is hard/md5.txt ?1?1?1?1?1?1 -o /root/Desktop/hash is hard/result.txt
------------------------------------------------------------------------------------------------
--pw-min is a reserved parameter for PRINCE attack mode
=======================================================
what's wrong !!!!!!!!!!!!!!!!!!!!

great symphony; )
Ответить
What an idiot to use that music for this topic, extremely irritating
Ответить
and... when I try this myself it finishes extremely fast, like 1 second, and i go into my folder and there is no password
Ответить
What are you attacking in this video? And how do i use hash to attack things like email?
Thanks.

how can i got someones hash codes
Ответить
I don't understand the hash thing
Ответить
Where did you get the hash.txt file from?
Ответить
what linux is this and what theme
Ответить
Noob question. How do you get the hash data in the first place? Are they in cap files? I have a cap file with handshakes that I uploaded to Hashcat to convert to hccap, followed the command in the tutorial but I get a "No hashes loaded" back from HC. I'm not sure what's going on lol
Ответить
dove trovo il codice sha-1 di un profilo facebook??
Ответить
Could I use this for a router settings username and password bruteforce attack?
Ответить
Is hashcat pre installed when i download kali
Ответить