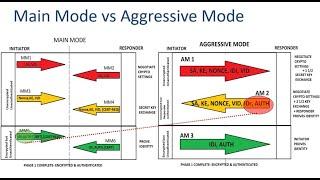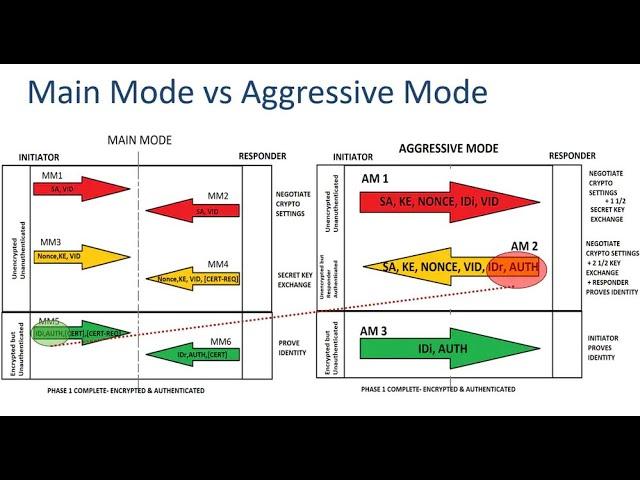
Main mode vs Aggresive Mode- IPSEC Training in 30 minutes
Комментарии:

Best Video
Ответить
Graet explications
Ответить
Awsome explainations
Ответить
clear cut explanation sir ! Thank you so much for the clarity about Ipsec.❤❤
Ответить
Best
Ответить
Maja nehi aya .... video lenght is too much....
Ответить
Great Content. Is it possible to get a hold of this VPN Prsesntation1.pdf file?
Ответить
Hi...Thanks for such good presentation and informative video. One suggestion from my side, Can you please add sequence of video link in description of IPSEC ?. Its easy for user to get know from which video he should start to know details on IPSEC protocol.
Ответить
I really like your lecture but have a couple questions.
1 - You mention that IKE phase 2 is like a data plane. I'm not sure I see this. I would call ESP and AH the data plane - they are the payload. IKE (ISAKMP & NAT-T) are your control plane -- they authenticate the peers mutually, setup the sessions and handle key negotiation. The management plane might be something like if you had some SDN that was automatically creating and tearing down tunnels. Yes, the ESP is still inside UDP 500 or UDP 4500 but it's not really a phase 2 negotiation, it's just taking advantage of the encapsulation transport provided by UDP.
2 - Around 30 minutes you ask the students where the key is coming from and you call DH the correct answer. Here I am thinking this is wrong. The diffie hellman is used to provide PFS of the IKE traffic. There is a PSK (or public keys) in use to secure the IKE traffic between the two peers. Without DH, an eavesdropper could take your conversation, brute force it offline, and figure out the PSK (or private keys). DH helps protect against this by creating a session key but only for IKE transport. Now the attacker would have to both know the PSK (or private keys) AND intercept the traffic and re-write it between both peers in order to see the traffic. Intercepting is harder than eavesdropping. So I understand the use of DH for perfect forward secrecy, but are we positive the key used in DES/3DES/AES256 comes from diffie hellman? Are we sure it doesn't come from somewhere else?

Excellent Explanation
Ответить
In the fifth and sixth packets of the Main Mode's SA negotiation when using IKEv1. What is the Identification payload ?From what I understand, when using PSK, this gets set to the IP address of the VPN peer, which can already be found in the source IP field. The source IP field might not be encrypted, but so what? Is there some advantage to having this same IP information encrypted?
Ответить
6 main +6 (3 *2 - unidirectional tunnel) quick mode messages are exchanged by isakmp ,So where i can we see " ike "in wireshark ???Encyption odf user payload is done using ESP.
Ответить
Nice explanation
Ответить