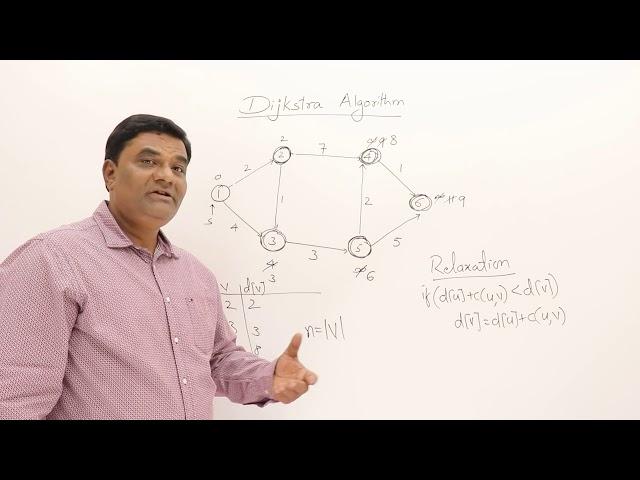
3.6 Dijkstra Algorithm - Single Source Shortest Path - Greedy Method
Комментарии:

Sir what is the application of this algorithm
I mean where we can use this algorithm sir.
Could you please tell me in detail....

I believe even Edsger Dijkstra would not be able to explain this so clearly
Ответить
Easy pzzy
Ответить
Thanks a lot for your explanation
Ответить
Thank you sir❤
Ответить
Thank you
Ответить
Thanks Sir for all your videos, this are helping me to know more about the pattern in solving algorithm.
Ответить
One of the best teachers in my life. Though he is not teaching offline but the way he explains and makes the difficult topics very easy is priceless. Thank you Sir.
Ответить
thanks
Ответить
Bro it so simple my prof cannot explain that good
Ответить
Huccha agud ond baki 🥲🥲🥲
Ответить
So basic difference between this and bellman ford is:
1) For Dijkstra, because of the limitation to explore only the unvisited nodes from current node( that we are considering) , the distance can be wrongly calculated (if edge is neg).
2) For bellman ford, we explore all the nodes reachable from the current considering node(weather they are visited or not), so it gives the correct answer( even if it has negative edge)
To Note : if the negative edge causes a negative Cycle then the bellman ford also identifies the occurrence , with its second check method) and throws an error(or notifies) and ends the algo.
Pls let me know if my understanding is correct (or if i'm missed something)

this guys the goat for all comp sci and cyber security students truely the goat
Ответить
This channel is a cheatcode
Ответить
perfect teaching
Ответить
Five Year Ago The Playlist was Uploaded
But still no one can compete it
Thanks Alot For Such a WonderFul Playlist For Free

Awesome job explaining this, it was very clear!!!
Ответить
can we start from node 6th. then the answer is different
Ответить
Well explained Sir
Ответить