Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Комментарии:

John Kent - 28.01.2018 23:05
Great lecture
Ответить
Frans Mulder - 17.01.2018 10:35
Great presentation
Ответить
Terry M - 15.01.2018 00:38
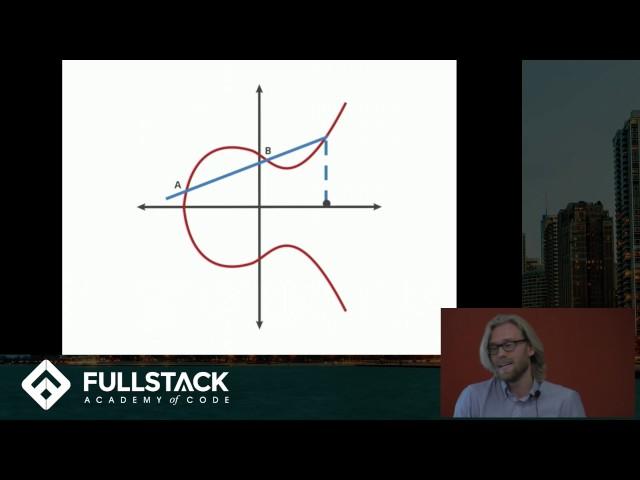
Is that a dot product?
Ответить
Steven Kifer - 30.08.2017 01:17
Great job. Thank you for the primer on elliptic curve cryptography. When you mentioned vulnerabilities of the DH key exchange, I was expecting you to mention the vulnerabilities of a MiTM attack where an attacker intercepts and throws away the shared values and passes along it's own made up values to each recipient. I wasn't aware of an attack vector that uses algorithms to make crunching the key easier. I'll have to look into that.
Ответить
Не получается похудеть? Причины почему не получается похудеть | Диетолог Андрей Никифоров 12+
Андрей Никифоров | Диетолог
Bell MITD - David Pares - Space Warp Technology
Art Bell on Periscope
Новогодний Голубой огонёк на Шаболовке - 2024
SHOW&CONCERT
Adam Savage's One Day Builds: Gaslamp Lantern Prop!
Adam Savage’s Tested
I Survived 24 Hours in the Deep Dark...
JesterBoogie
Only the Strong Will Survive
Axel Rudi Pell - Topic









![[Free] Yeat Type Beat - ''Rich talk' [Free] Yeat Type Beat - ''Rich talk'](https://invideo.cc/img/upload/UXVoV1BxUlJJWms.jpg)















