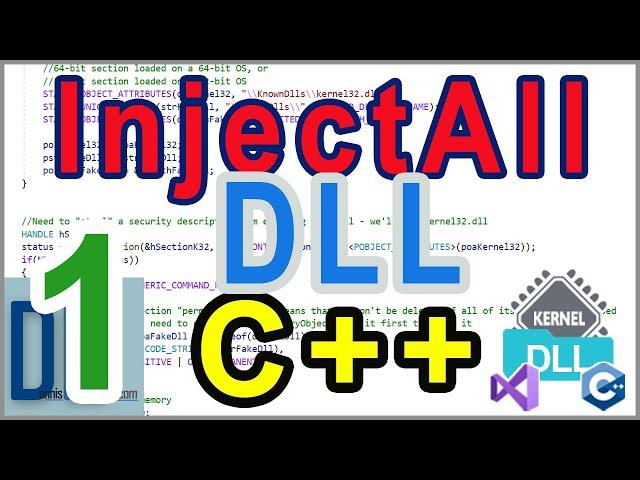
DLL Injection Into All Processes - Part 1 - Installing & Setting up tools, Basic Concepts
Coding it in WinAPI/C++ using Visual Studio - Installing & Setting Up Tools, Basic Concepts
Blog post: https://dennisbabkin.com/blog/?i=AAA10800
0:00 Into
1:31 Setting up virtual machines to run driver tests in
4:22 Setting up Visual Studio components needed to code our project
7:00 Setting up tools in a VM:
7:44 Process Hacker - to view running processes & modules:
https://processhacker.sourceforge.io/
9:36 DebugView - to view debugging output from our driver:
https://docs.microsoft.com/en-us/sysinternals/downloads/debugview
11:16 WinObj - to view kernel space objects:
https://docs.microsoft.com/en-us/sysinternals/downloads/winobj
11:55 PEInternals - to statically view PE files:
http://www.andreybazhan.com/pe-internals.html
13:11 WERSetup - to set up Windows Error Reporting to catch user-mode process crashes:
https://dennisbabkin.com/wersetup/
15:19 WinAPI Search - to check Imports/Exports from PE files and to search for error codes:
https://dennisbabkin.com/winapisearch/
16:53 Driver Loader/Unloaded - to register, start, stop and unregister our driver:
https://dennisbabkin.com/driverloader/
17:37 Putting the Operating System in a VM into a test signing mode to be able to run our driver:
https://docs.microsoft.com/en-us/windows-hardware/drivers/install/the-testsigning-boot-configuration-option
19:52 Creating a snapshot in the VM in case we mess up the operating system during our driver testing
21:20 Quick overview of: physical/virtual memory, and of DLLs/modules/"sections" in the kernel space
30:34 Overview of DLL injection with the PsSetLoadImageNotifyRoutine function
31:13 Basic overview how we can inject our DLL into every process
#kernel #driver #tutorial #cpp #win32
Blog post: https://dennisbabkin.com/blog/?i=AAA10800
0:00 Into
1:31 Setting up virtual machines to run driver tests in
4:22 Setting up Visual Studio components needed to code our project
7:00 Setting up tools in a VM:
7:44 Process Hacker - to view running processes & modules:
https://processhacker.sourceforge.io/
9:36 DebugView - to view debugging output from our driver:
https://docs.microsoft.com/en-us/sysinternals/downloads/debugview
11:16 WinObj - to view kernel space objects:
https://docs.microsoft.com/en-us/sysinternals/downloads/winobj
11:55 PEInternals - to statically view PE files:
http://www.andreybazhan.com/pe-internals.html
13:11 WERSetup - to set up Windows Error Reporting to catch user-mode process crashes:
https://dennisbabkin.com/wersetup/
15:19 WinAPI Search - to check Imports/Exports from PE files and to search for error codes:
https://dennisbabkin.com/winapisearch/
16:53 Driver Loader/Unloaded - to register, start, stop and unregister our driver:
https://dennisbabkin.com/driverloader/
17:37 Putting the Operating System in a VM into a test signing mode to be able to run our driver:
https://docs.microsoft.com/en-us/windows-hardware/drivers/install/the-testsigning-boot-configuration-option
19:52 Creating a snapshot in the VM in case we mess up the operating system during our driver testing
21:20 Quick overview of: physical/virtual memory, and of DLLs/modules/"sections" in the kernel space
30:34 Overview of DLL injection with the PsSetLoadImageNotifyRoutine function
31:13 Basic overview how we can inject our DLL into every process
#kernel #driver #tutorial #cpp #win32
Комментарии:
PRX vs DFM - DRX vs TE - KNOCKOUT - DAY 7 - VALORANT Radiant Asia Invitational
VALORANT Champions Tour CN
The Wild Robot (J.B. Eagle Style)
J.B. Eagle
Celebrity Death Prank Tiktok Compilation
AllStar Compilations
ПОДРУГА СОЗДАЕТ СКИН ОНА ЗДЕЛАЛА КРАСИВЫЙ СКИН?! -KONFETKA.PLAY
-𝑫𝒊𝒏𝒂𝒓𝒂'𝒔 𝒍𝒐𝒗𝒆.🎭💤



![Stray Kids [INTRO " (5-STAR)"] Part 3 : Recording Stray Kids [INTRO " (5-STAR)"] Part 3 : Recording](https://invideo.cc/img/upload/UWZHWG5qLXROXzg.jpg)