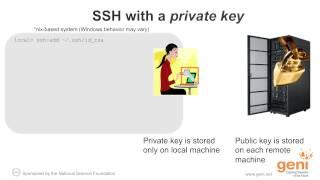
Комментарии:

Can barely hear anything :(
Ответить
Can't hear you!
Ответить
Nice explanation. You have a calming voice!
Ответить
Try yardtools on instagram, he's the best to get your work done.
Ответить
I recommend erictoolls on instagram or whatsapp *16572076574 to you all to help you out cause he finds solution to every of my problems.
Ответить
hiddentoolz on lg.. best ever on prvt keys, thanks to those who recommended them❤️🙌
Ответить
1805codes give the real 🔑 key 🔐 he on iG
Ответить
volume is very low
Ответить
NSF should get my money back from this video uploader
Ответить
Are you talking or crying? I need a 200W audio power amplifier! ;'D. Anyway, nice video. Next time try to improve on the recorded audio level. thanks
Ответить
Download Audacity. Download Lame for Audacity. Put in your audiotrack. Click amplify. Click ok. You're done
Ответить
Good video and to the point. Audio was a bit low but I could live with that.
Ответить
Q: gerrit for example , we now understood that public's stored in server , private key within client PC, as your video shows.... the thing is, after client account authentication passed, how normal data transfer be encrypted? Server encrypt data with public key, send these data to client , and then these data're decrypted by client with private key. but what about data direction from client to server ? who takes charge to encrypted ? thx
Ответить
Speak out woman!
Ответить
Very helpful, audio could've been better!
Ответить
great explanation!
Ответить
Try to speak louder
Ответить
yells WHAT?
Ответить
Stupid video, I wanted to know how it works, bit not how to use it!
how does remot server know which one key to use? Both local server and remote one can have thousands keys installed!

Voice is very low, I tried to listen twice but could not hear it. Maybe I will try with external speakers.
Ответить
The video makes me tune up the volume twice.
Ответить
Thank you for the video. One constructive criticism... You mention having one key to log onto many servers. This is incredibly un-secure. This would mean that if your key was stolen or compromised then you have also made vulnerable all of your servers. It is much safer to have separate key pairs for each server.
Ответить
Audio sucks.
Ответить
Not to mention it also makes executing connections to other servers via a script much easier. Great explanation.
Ответить
Thanks, this was very helpful!
Ответить
Thanks for video! This is explained well.
Cheers!!