Комментарии:
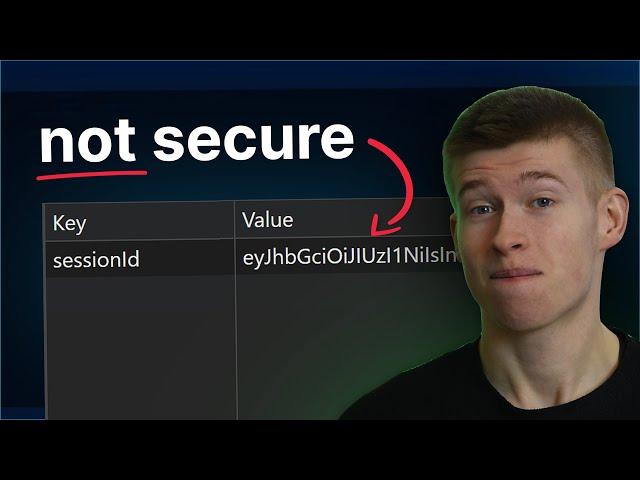
LocalStorage was a mistake...
Josh tried coding
2Pac Type Beat flash life 2024 , 2pac instrumental
DJ I S R A E L . F
Asmr Católico | Hablemos de los apegos y las riquezas
Joha Atehortúa
Configuring NTP on a Linux client
tekopolis
FAIDE IS JUST INSANE IN NEW E -DISTRICT MAP - APEX LEGENDS
24 GAMING VIRAL CLIPS
Замена амортизатора на снегоходе, от нивы 214
Александр Богданов
АСМР УКОЛЫ КРАСОТЫ И МАССАЖ В ТРЕШ САЛОНЕ
ASMRCatherine
Goyang Dhea zhauta,GPS bergoyang
ebi ci di ki