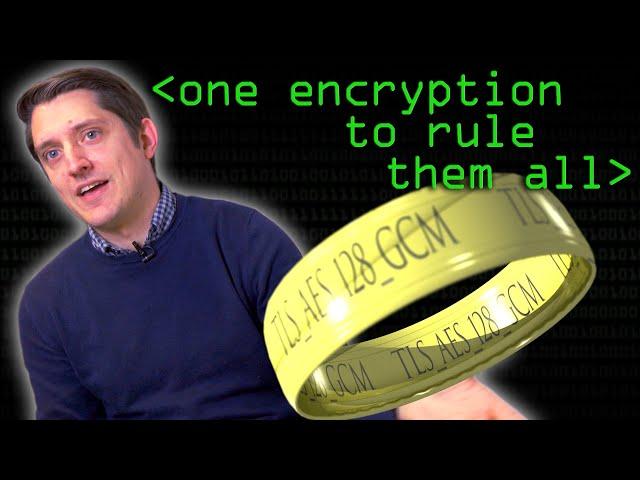
One Encryption Standard to Rule Them All! - Computerphile
Комментарии:

one ring to rule them all
Ответить
Joan Daemen is my professor at Radboud University, so awesome to be taught by one of the best :D
Ответить
When he says "sp networks", all I hear is "yes peanut works". I might just be hungry.
Ответить
I am going to attack the AES. Hopefully I can break it.
Ответить
thanks
Ответить
What does it mean for encryption to be able to work on a hardware level? I'm confused how that works
Ответить
"Not me, I was quite young at the time"
He would have aced it nowadays obviously

I hope one day we will see a video about DES
Ответить
For one second there I thought the guy was Ted Chaough from Mad Men.
Ответить
One encryption standard to fail us all. When a vulnerability is found.
Ответить
I like this channel, I will subscribe immediately.
Ответить
There always seems to be a metric of, one super computer working on this problem. What about if it's spread across thousands of cpus, each attacking a different segment of that 2^128?
Ответить
This person is solely responsible for reigniting my interest in academic research. Hope he makes more videos.
Ответить
..., one encryption to find them. one encryption to bring them all, and in the darkness bind them.
Ответить
This man is genius!!! I like the way he explains cryptography and complex things.
Ответить
Thank you
Ответить
so frodo did keep the ring
Ответить
Hahaha this guy gets himself into like 1000 more videos with every video he's in.
"We'll talk about that more in another video"
"We'll go into greater detail on that in another video "

i thought that he was going to talk about "ryan dahl", the creator of node.js
Ответить
Correct famous algorithms suitable but they aren't limits by input parameters but change it often that create in security by process too. 😃
Ответить
Aaay so we Belgians have something to be proud of at least ^^
Ответить
Meu amigo gosto muito do seu canal que Pena que não tem a legenda em cima português???
Ответить
He has zero understanding of the power of quantum computers.
Ответить
isn't triple DES done with 2 keys?
Ответить
One ring to rule them one.
Ответить
"It will take millions of years to break"
That is only if you assume that you buy the hardware today. And thus this is a very wrong assumption.
2^128 is a large number: 3 * 10^38.
Assume you can test 1 G keys per second today, and hardware gets 2x faster every 10 years. That is a fairly modest assumption today.
In the first 10 years you will have tested 10^9 keys/s * 3*10^7 s/year * 10 year = 3*10^17 keys.
In the next 10 years you will have tested 2^1 *10^9 keys/s * 3*10^7 s/year * 10 year = 6*10^17 keys.
In the next 10 years you will have tested 2^2 *10^9 keys/s * 3*10^7 s/year * 10 year = 12*10^17 keys.
...
In year 300-309 you will test 2^30 *10^9 keys/s * 3*10^7 s/year * 10 year = 3*10^26 keys.
...
In year 700-709 you will test 2^70 *10^9 keys/s * 3*10^7 s/year * 10 year = 3*10^38 keys.
So even with very modest assumptions we are not talking millions of years, but instead 700 years.
And if we assume hardware and better algorithms improve by 2x every year (which historically is closer to reality) then we are talking 70 years.

Why not go with Serpent now that computer are way faster and multi-core, 8-16 cores is now common, more secure and would be practically unnoticed; we reinvent the wheel because better wheel. At least an evaluation and real-world practical index should exist, if the usefulness is too low and the security will increase too little for the added power and time consumption by the extra processing, them sure, it's not worth it, but such assessment should occur by the Cryptocommunity
Ответить
My dad is a journalist and he interwiewed Rijmen en Daelen and they said that they made the name do that english speaking people would'nt be able to pronounce it and ...
Ответить
well quantum computers are gonna destroy these keys now. So, we're going to have to come up with a new encryption. If that's even going to be possible.
Ответить
des cats three times
Ответить
Vincent Rijmen is my prof at my university :D
Ответить
I could listen to him talk all day!
Ответить
Coincidentally TrueCrypt uses the three of AES, Serpent and Twofish chained together to encript its data
Ответить
Is it just a coincidence that the views are on 256k or am I tripping
Ответить
In physics, a chain is only as strong as its weakest link.
However, in cryptography, the inverse is true. The message is as secure as the strongest method used. Yes, I am talking about "daisy chaining" crypto systems.
1. ROT 13
2. AES.
You can't get to the super simple ROT 13 unless you first break AES..

I'd like to see a video on the CAESAR crypto competition one day. And the SHA-3 process as well.
AFAIR (from classes taught by the man himself, though it's a handful of years ago), Lars Knudsen (from the Serpent team) agrees with the choice of Rijndael as AES. Not so much with Keccak as SHA-3.

p hoblm
Ответить
Here’s an idea: Quadruple DES
Ответить
Chacha20's design wasn't just to make it faster in software using conventional hardware. It also designed to avoid side channels in software implementations.
Due to fast implementations of AES needing lookup tables the key can be inferred due to timing differences. (Also the sound the CPU makes which is freaky)
Chacha20 is also seekable, if you have encrypted a 20GB block and you want to read the end of it. In AES-GCM you'd decypt the whole block. In ChaCha you can decrypt any part of the sequence.
(Also XChaCha20 is now used in TLS 1.3)

Keepass uses two fish.
Ответить
Can't believe OpenSSL is mentioned as a standard implementation...
Ответить
Once back door to rule them all.
Ответить
What if internet is in the equation. I don't know the details but some people use "trojan like" softwares to make your computer a slave or maybe a joint voluntary attack using the computers of people around the world to brute force stuff ?
Ответить
Can we look at post quantum encryption standards please
Ответить
Is the ring in the thumbnail a reference to digital fortress?
Ответить
![CS:GO - ENCE vs. G2 Esports [Nuke] Map 2 - Group A - ESL One New York 2019 CS:GO - ENCE vs. G2 Esports [Nuke] Map 2 - Group A - ESL One New York 2019](https://invideo.cc/img/upload/a1FRRFBmVmhDOFg.jpg)







![[4K] Try On Haul | Get Ready With Me | Trying on stockings | See Through and No Bra [4K] Try On Haul | Get Ready With Me | Trying on stockings | See Through and No Bra](https://invideo.cc/img/upload/QVAzd1RERXhIVHQ.jpg)














