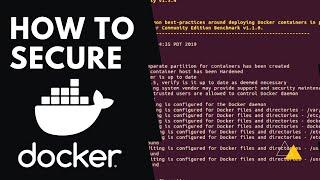
Docker Security Essentials | How To Secure Docker Containers
Комментарии:
Turn OFF iCloud Music Library on a PC
Northville Tech
Influencers are LYING about Side Hustles! "$100K a month?"
Isabella Lanter
پدر و مادر و من کجا هستیم،چرا ویدیو نمیگذاریم؟
Sohaila&Murtazaسهیلاومرتضی
Frog fish in lay down! #thatswhatidooutdoorz
#thatswhatidooutdoorZ