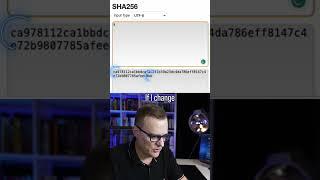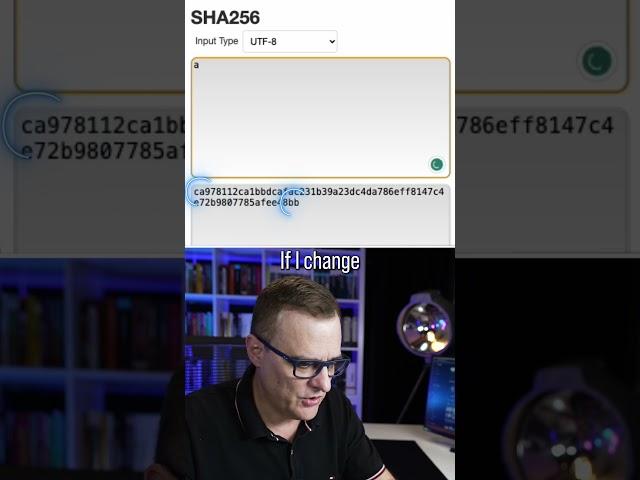
Is Hashing Encryption? #shorts #encryption #hashing #password
Комментарии:

Danke boet.
Ответить
I need hash to understand hash
Ответить
One thing I don't get about verification is what would happen if there is a hash collision like two very different inputs but same hash value
Let's say "veryoriginalpassword" has the same hash as "mygoodpassword" how would hackers use it to their advantage? Would they be able to access the user just by using the hash? (I have the idea that they would just attack the password, like they just need to bypass the hashing part and be able to validate it, but I don't know)

Hi I need to do this
Ответить
As is shown, by the fact that the hash remains 256 in length, there is a potential for more than one input value to compute to the same hash, very unlikely to be found before lockout of a bruteforce attempt, but that is why the length of hashes has become the measure of its strength. So it means you more than likely have the original password value, with high confidence, not 100% certainty.
But I ain't one to gossip... .
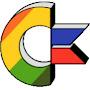
It is not a pseudo random number. It is totally derived from the input - if I input 'a' I always get the same output - and using SHA256, you'll get the same answer on every machine.
Ответить
Yes I can decrypt hash😅
Ответить
Pretty sure this is how Heroes three battle algorithm works too. There's only one outcome for every action, in a chain of events.
Ответить
Bonus: there are various input values that will generate the same hash value. But it would be impossible to identify them, even if you knew the hashing algorithm, short of running a brute force database of all possible inputs and their resulting hashes.
Ответить
Thank you!
Ответить
the only problem with that.. 2 different inputs can generate the same hash... so
Ответить
But if the complex algorithms were somehow configured, you could technically decrypt it right?
Ответить
Isn’t prett much like checksum or similar !?
Ответить
But these are not secure right?
When a person hash code of all possible word, he can know the value we're passing right?

Interesting
Ответить
Thank you
Ответить
That's not true
It is not one way. Yes, it is extremely hard to decrypt, but technically, it is double

So whats the point of it? If I use a password without hash, you still need to check if the password is the same as you do with the hash
Ответить
Hello sar aapke dwara video gyanvardhak bataya gaya hai bahut acchi baat hai per main Bharat Desh ka Rahane wala hun Bharat ki baat batata hun is Desh mein itne bade bade hacker hain aap kitni achcha password dal dijiye vah Tod dete Hain aur aapka bank account Tak Khali kar dete hain aur sarkari karmchari bhi apradhon mein lete Hain
Ответить
suggest me some online training course where i can learn Cyber Security and get a job . I am from NOn-CS background
Ответить
Similar to crc Circular redundancy check
Ответить
Thats why i love rainbow tables 😅
Ответить
I never use real words or meaningful passcodes.
Ответить
❤
Ответить
Do you have any recommended resources for learning to design and create hash functions? I tried looking into it once and came back with a bunch of abstract papers explaining the need for them.
🤍

So if I understand this right, when someone types in a password that gets turned into a hash and store it under the email and set that as one email and password combination. And everytime they type their password, that encrypts it as a hash and sees if it matches with the hash that is connected to that specific email address.
Ответить
Your ending was wrong. You assumed when hashing two passwords results are always the same well, it depends on the type of hash function used, look at a Salted Hash.
Ответить
What the Hash!
Ответить
Make one about salting
Ответить
Do you think facebook stored our password as a hash?
Ответить
Aaaah nice reinforcement
Ответить
What about using cryptanalysis to get the hash back to original data, isn't it easy if you know the hash algorithm, so doesn't it become like decrpytion.
Ответить
you earned a new subscriber :)
Ответить
So is hashing used for passwords authentications ?
Ответить
But doesn‘t that mean that there is more than one input, that gives the corresponding output? The size of the hash doesn‘t change, so there is a limited amount of information stored in that hash. In this case it should be ~10^77; So, theoretically, if you were to make a bot, so fast, or with so many threads, that it could produce more than these 10^77 possible outputs, at least one output should appear twice. This, at the same time, would mean, that you could give it a random set of numbers/letters/whatever and perchance it would work (it is not very likely (2/10^77), but hey! It‘s worth a shot, isn‘t it?)
Ответить
All sudo
Ответить
Just create complicate password without hasshing still should work
Ответить
What about "You've been changed this password, please make a new one!" or something like that when we resetting password? Isn't that mean 'they' know our old password?
Ответить
Salam
Heard David Bombal all over when Researching cybersec resources, but mannn, I get it why! From just 1 short! You really are a very good teacher. That explanation style which just so smoothly gets into head. Kudos!

thanks
Ответить
Could you theoretically decrypt it?
Ответить
Sir I want to hack wifi network of my friend what simple method did I use?
Ответить
so that's How jt helps in Brutforce.🎉❤
Ответить
Ok but it's NOT a 'computer networks only' thing
Ответить
Dude you are too generic. It depends on the type of hashing. There are reversable hashes. You are picking non reversable method and say all types of hashing is non reversable.
Ответить
Is that how they store passwords in apps?
Edit: you said it literally as I posted my comment. Thanks!

Bro which link is used to hash
Ответить
So it still doesn’t secure simple passwords like “p@assw0rd” or “qwerty” as hash for those is know, right?
Ответить
我如何从钱包中将我的 89 USDT TRC20 提现到币安请帮帮我 12个钱包恢复短语:『pride』-『pole』-『obtain』-『together』-『second』-『when』-『future』-『mask』-『review』-『nature』-『potato』-『bulb』
Ответить
Did you know this? Hashing is so important in todays' world!
Ответить