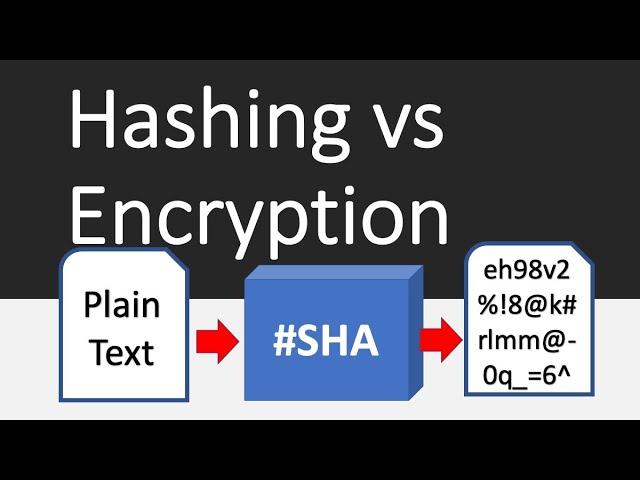
Hashing vs Encryption Differences
Комментарии:

Excellent material. Thank you!
Ответить
That Was Great !
Ответить
how is classical symmetric cipher different compared to modern cipher ?
Ответить
Thanks
Ответить
Great explanations, thanks a lot!
Ответить
This is my first time watching one of your videos and I loved your teaching style. Subscribed!!
Ответить
Hello - World.... I like what you did there, lol!
Ответить
This lecture is golden!!
Helped me clear a lot of basics and really understand the concepts!

Fantastic explanation. Thank you!
Ответить
One argument I heard from cryptographers pondering about the futility using 'salt' is that if someone has access to the database where you store the hashed passwords, the attackers already had access to your critical data anyway.
Ответить
Mallory 's hairdo alone is criminal!
Ответить
your example why MD5 isn't secure doesn't really show anything. Its equally easy to generate table would it be 128 bit or 512 bit hash. Otherwise awesome video.
Ответить
Excellent video and explaining the technology. However, I have a situation where I don't know how I would adapt the concepts you explained because the scenario is slightly different. Your example works interactively by comparing user passwords with stored hash values. My scenario is for an automated process (no user interaction at all) and the credentials are self-contained in the program package. These must not be known to the user or anyone who can get a hold of the file(s) containing them.
Here is a live example … We have a company application that requires administrative rights to execute but our users only have standard Windows user permissions. I repackaged the application into a single EXE executable script to conceal the admin credentials that are included in the script code. However, I discovered that compiling the script is not enough because the EXE file can be decompiled or someone can use other programs to see the contents.
How can I adapt the concepts you explained in your video this my scenario? I need to be able to execute a self-contained application package locally (no network or internet resources) and with specific credentials while protecting said credentials from the local user or anyone who might get a hold of the EXE file containing the credentials. The application needs to use these credentials at run time to perform its tasks.
Your insight is most appreciated.

"never see Windows or Mac again in your life"
deal!

💙💙
Ответить
these 'keys'.... would you encrypt your 'private key' in case someone tries to steal it?
Ответить
Great explanation, Thank you very much
Ответить
Awesome Awesome 🤩 . I’ve learned a lot!🤝
Ответить
The joke at the end..🤦🏿♂️
Ответить
Amazing!
Ответить
Excellent, just excellent.
Ответить
Wow! Awesome explanation sir.
Ответить
Great explanation... Thank you very much!!!
Ответить
This is a great video! Your explanation is very to the point without any fluff and presented in a way that doesn't make me wander to the next video. Thank you for the information in such a presentable way!
Ответить
Aaaaand, now I get it. THANK YOU!
Ответить
This is such an amazingly created video. Thanks for covering the multiple related aspects in one crisp video.
Ответить
This was super informativem thank you!
Ответить
I wish you were in my country to solve all my hashes and keys - Purchase from 2010 N 2011 N 2013 😥
Ответить
Amazing
Ответить
Commendable explanation.
Thanks for sharing.

wow, thank you so much. "... never see a windows or Mac ..." joke cracked me up 🤣
Ответить
But if the hasing value also changed according to changed document by attacker and give to receiver
Ответить
Thanks for the video Professor. Very clear explanation to follow. Hashing technique was particularly useful for us in de-duplicating big data sets. Have shared it in a video.
Ответить
Main difference is that encryption is 2 way(Can be reverted to original string),
and Hashing is 1 way(Cannot be reverted to original string)

the common practical way:
1) encrypt+hash+salter
2) Data send through encrypted package
3) Unencrypt the received data
4) Check on the hash and token should return valid/true.
5) do the things...
Regarding MD5, shouldn't really use it, if still insisted, must merge with add-on unique hashing algorithm to generate the only unique result.
In reality, there are still tons of systems still using the MD5 hashing basis but they modified with other unique hashing algorithm.

top video
Ответить
That video is gold, thank you!
Ответить
goat
Ответить
Love this channel
Ответить
Amazingly well explained sir. Very grateful for it. Subscribed.
Ответить
Thanks lots Pro you make it clear even though im not computer background
Ответить
Damn this is good , not good amazing !
Ответить
Thank you sir!
Ответить
Hi, how can 64 units represent all the combination of all the files and or passwords in the world? thank you
Ответить
Thank you so much for this video! Enjoyed it
Ответить
Thank you professor Sluiter
Ответить
BEST! 🧨🔥🔥
Ответить






![Cumbia 85 - Yahir Saldivar - [Letra] Cumbia 85 - Yahir Saldivar - [Letra]](https://invideo.cc/img/upload/MDZTOGhkckczNXo.jpg)