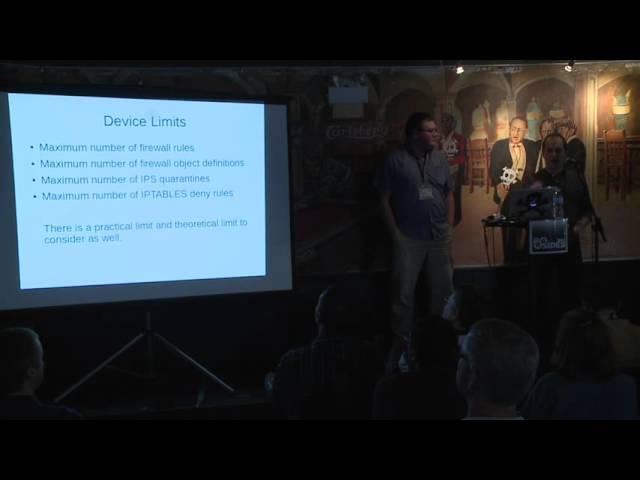
BSidesTO 2015 - Allan Stojanovic & David Auclair - MOAR Logs and Tactical Defence
Previously on Logs and Tactical Defence (https://youtu.be/f48lOuHmVxI), we outlined a few simple recipes to detect questionable activity, determine the attackers' intent, and respond in traditional and novel ways. In this presentation, we will detail some new recipes, show some interesting failure modes for some of the old ones, and discuss the operational overhead of running such a system.
Тэги:
#BSides #BsidesTO #2015 #infosec #security #TorontoКомментарии:
Contact Center Software
Talkdesk
МЕСТНАЯ ЗНАХАРКА / СЛУШАТЬ АУДИОКНИГУ
БЫТОВЫЕ ИСТОРИИ / АУДИОКНИГИ
How To Link EA Account To Twitch FC 24 !
Genie Guide
Knowlarity : Cloud Call Center Solution
Knowlarity
HOW TO Link your EA account to Twitch / Youtube and EARN REWARDS
Flair's EAFC Tutorials
How Much Does Call Center Software Cost?
CloudTalk








![[FREE] dj screw type beat - ride [FREE] dj screw type beat - ride](https://invideo.cc/img/upload/TXFWZGZQWTZBako.jpg)