Комментарии:

Great Video. One question, how often does that process kick off?
Ответить
What I dont understand is how this makes the data secure by any means, cant a cleverly designed software follow all this communication and end up with the same symmetric key at the end (assuming the attacker is able to sniff every single package sent back & forth)?
Ответить
Perfect explanation. I thought every time we encrypt with server certificate public key the whole time but it's not.
Ответить
Where is the CA (Certificate Authority)?
Ответить
Well explained. thanks a lot 👍
Ответить
Epic Video!
Ответить
each client generates a unique symmetric key, how does the server stores all these symmetric keys ? if million unique users hit a website does that mean that the server stores million symmetric keys?
Ответить
another good explanation need to watch a few times
Ответить
Thank youuu
Ответить
Wow, it is amazing to know what happens behind the scenes. I would like to meet the people who create/invent these things.
Ответить
amazing and easy to understand
Ответить
Does it protect TCP header and payload both? Or just the payload?
Ответить
super fkng awesome explaination
Ответить
Nice explanation! Thank you.
Ответить
Very well explained, thank you.
Ответить
Best explain I'd ever seen.
Ответить
nice 🔥🔥
Ответить
Very well explained, pretty useful.
Ответить
amazing vid thanks so much
Ответить
Hi all
Is anyone can help me here if i disable TLS 1.0 and enable TLS 1.1 and 1.2 then my crystal reports is not working

Its really amazing explanation on TLS handshake Thank you ... Just for my curiosity which application you used to record video with screen whiteboard option.
Ответить
That was entertaining to watch :)
Thanks.

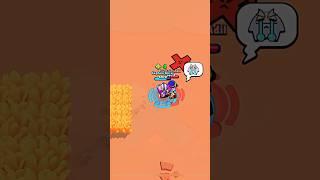
I don't understand when Difie Hellaman is used here. And why is it actually needed? Why a signed certificate with public key is not enough?
Ответить
Thanks and that was great video. Have one question in the actual data transfer , the data is encrypted with symmetric encryption and the symmetric key is encrypted with asymmetric encryption for each session?
Ответить
Wow this is great. It takes months to truly get your head around this but vids like this make it so easy to refresh my memory
Ответить
Thank you for explaining things perfectly!
Ответить
what technology is he using to present? Is this a camera trick or a special screen?
Ответить
What's the point of encrypting the pre-master-secret using the servers public key? Wouldn't the man in the middle know the public key of the server, so the man in the middle could decrypt the pre-master-secret.
Ответить
cool presentation. Questions: is the pre-master key actually exchanged, if so, what if man in the middle learned it, can it be used to create the eventual asymmetric key? Meaning during the TLS handshake is there vulnerability? 2nd question, is the final symmetric key ever exchanged? thanks.
Ответить
I got everything but I have a single doubt. Pre master secret is derived from public key. And then it is encrypted and shared with the server. And then server has the same pre master key. And now both client and server makes a symmetric key. How? What kinds of algo do they use? And how do they ensure that they make the same symmetric key?
Ответить
Wow ...
Ответить
The most thorough explanation of TLS Handshake. Thank you!
Ответить
im a little confused... wouldn't it suffice if only one side generated a symmetric key? why is it necessary that even though it's the same symmetric key in a way another one would be generated by the web server?
Ответить
Does symmetric key encryption used on top of the asymmetrical encryption, or do both nodes switch over to symmetric encryption? If so, why not asymmetrical to host and symmetric back to client?
Ответить
Very Informative, thanks
Ответить
Great explanation. Breaking something down that takes microseconds to complete into a 12min video.
Ответить
no such thing as hellox or handshakex etc about it, ts just machinex, no nerx, cepitxuxyuax, any say any nmw
Ответить
The waterfall analogy was outstanding, provided an excellent framework for further study.
Ответить
As far as i know there's nonce in the handshake process. I know it's used to prevent some replay attack but I wonder if nonce is used to create pre master secret.
Or Is pms only genereated from server's public key?

If anyone needs more deeper information then can check
ECC-based SSL handshake (ECDH- ECDSA key exchange). | Download Scientific Diagram (researchgate.net)

Superb!
Ответить
Amazing!
Ответить
after went through so many other videos. Finally got clear picture only from your explanation. Very good explanation, thanks !
Ответить
Great Video..!! One quick question.. How does the client verify that the (certificate and the public key) is coming from Big-IP not from an anonymous attacker?
Ответить
Man this is TECH NF
Ответить
But what is the pre master secret? ;/
Ответить
Excellent explanation. Thank you.
Ответить
Is this tls v1.3?
Ответить
Very good explanation!
Ответить
Awesome explanation.
But I didn't get the difference between Pre-master secret and symmetric key. As per my understanding they are different names to the same key. Could someone please correct me?

![How to Back Up, Restore and Exploit Saves With Checkpoint [Nintendo Switch] How to Back Up, Restore and Exploit Saves With Checkpoint [Nintendo Switch]](https://invideo.cc/img/upload/c1FMZExKa0hlb2k.jpg)